CMMC Enclaves
Need to Get CMMC Compliant, Quickly?
A CMMC Enclave Might Be the Solution!
Don't let compliance gaps hold you back from winning new contracts and growing your business. With a CMMC Enclave, you'll be able to meet compliance requirements quickly, while enhancing the security and operations of your business.


- Built for a Microsoft environment
- 365 GCC or 365 GCC High Azure
- Use your own devices
- Quick setup time
- Seamless integration with your workflow

- Built for a Google environment
- Requires new devices (Chromebooks)
- Quicker setup time
- Faster integration of sub-contractors
- Generally lower licensing costs
Which Enclave Is Best for My Business?
MNS Microsoft Enclave
![]()
- Microsoft environment
- 365 GCC or 365 GCC High Azure
- Use your own devices
- Quick setup time
- Seamless integration with your workflow
![]()
- Built in a Google environment
- Requires new devices (Chromebooks)
- Quicker setup time
- Faster integration of sub-contractors
- Generally lower licensing costs
Features of MNS Microsoft Enclave
- Microsoft 365. Work the way you are accustomed to working Using company-approved devices, experience an elevated workflow within the enclave, accessed seamlessly through a secure Remote Desktop session. The familiar Windows desktop enables efficiency and collaboration with essentials like Outlook, Teams, and Sharepoint with confidence in the data’s integrity.
- Enhanced Access Control. Advanced identity and access management solutions that ensure sensitive data remains accessible only to authorized individuals within your secure enclave.
- Data Safeguarded at Rest and in Transit. Customer-managed encryption keys, thwart unauthorized access and safegaurd the confidentiality and integrity of CUI.
- Proactive Threat Monitoring. Real-time Advanced Threat Protection (ATP) to detect and prevent phishing attacks, malware intrusions, and unauthorized data transfers.
- Regular Audits and Security Assessments. Vulnerability assessments, regular security scans internally and externally, and compliance reporting built into the enclave.
- Enclave Support from Experienced Service Provider and C3PAO. With more than 20 years of client business and technical support, staff is well provisioned for success and security.
- Data Loss Prevention (DLP) Strategies Implemented. Vital in deterring unintentional or deliberate data leaks and excel at detecting and preventing the sharing of sensitive information in line with NIST SP 800-171 and CMMC requirements.
- Effective Logging for Incident Response Audit logs configured and retained for the required duration. Security Information and Event Management (SIEM) system, serves as the central log repository and streamlines automated incident handling and remediation.
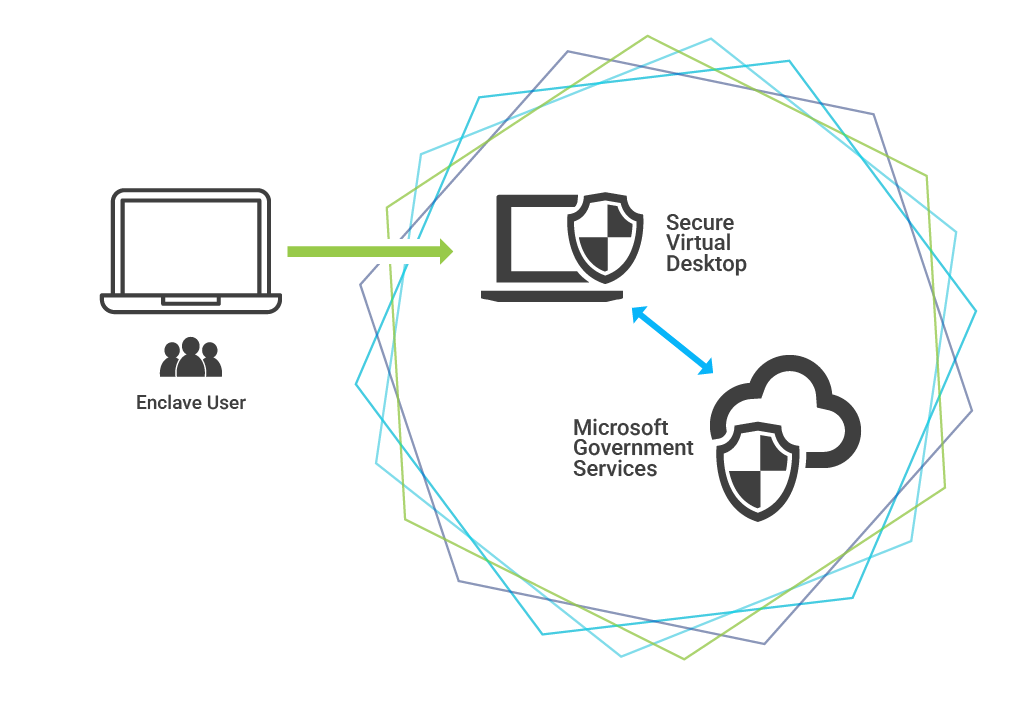
Why Use MNS Group's Microsoft Enclave?
- Streamlined timeline to Readiness. Pre-Configured Security and Compliance Controls eliminate the need to develop security measures from scratch. MNS Group’s Microsoft Enclave comes with pre-configured controls aligned with CMMC requirements, significantly reducing implementation time and the need for specialized expertise while ensuring your organization meets critical security benchmarks.
- Secure Collaboration Across Teams. Enable secure collaboration both internally and with external partners through encrypted communication and file-sharing tools. Microsoft Enclave allows teams to work confidently on sensitive projects—whether collaborating with subcontractors or federal agencies—while maintaining data integrity and confidentiality.
- Empower Remote Work. In today’s dynamic work environment, secure remote access is crucial. MNS Group’s Microsoft Enclave’s cloud-based infrastructure supports distributed workforces with encrypted connections and rigorous authentication protocols, ensuring that employees and authorized partners can securely access CUI from anywhere without compromising compliance.
The Benefits of a CMMC Enclave.
You can experience peace of mind knowing your data and systems are secure, compliant, and ready for work.
Establishing a CMMC Enclave accelerates your compliance journey, and provides a secure, isolated environment that meets required security standards.
By leveraging our Enclave, you can:
- Advanced Timeline to Compliance. The average enterprise-wide compliance implementation takes approximately 12-18 months. With an enclave customized to a scoped portion of your organization, compliance can be achieved in a fraction of that time.
- Focused Security at a Lower Cost. Security efforts and expenses are focused on the CUI assets. Only those users who access CUI are included in the enclave, limiting expenses on licensing, specialized support, and security provisioning.
- Simplified Tech Workload. Migrating the infrastructure of the entire organization is disruptive to operations and taxing on technical staff. An enclave’s selective approach limits such interruptions and can be deployed while the legacy system continues to operate. Existing technical staff resources are free to continue to support those systems.
- Scalability. The flexibility of the secure cloud environment scales easily so your enclave environment can adjust as your needs do.
.jpg?width=432&height=397&name=why-choose-enclave-graphic_reverse-(1).jpg)
Features of SecureCMMC™ Enclave
- Google Workspace: Work where your organization thrives. Self-contained, Scalable, Proven SecureCMMC™ leverages FedRAMP High-rated cloud solution to address security controls required to achieve CMMC Level 2 certification.
- Minimal Equipment. Google Chromebooks are the only physical assets required.
- Secure. Aligns with tenants of Zero Trust Architecture (ZTA) and delivers defense-in-depth by using end-to-end transmission and at rest encryption, Role-based Access Control (RBAC), automated configuration updates, and full ecosystem auditing.
- Affordable Licensing. Google Workspace Enterprise licenses provide an affordable, secure, and scalable solution to meet project, contract, and enterprise-level needs.
- Technical Support from Experienced Service Provider and C3PAO. With more than 20 years of client business and technical support, your staff is well-provisioned for success and security.
Why Use SecureCMMC™?
- Verified by DIBCAC. SecureCMMC has passed many DIBCAC High Assessment many times, and is the solution used and trusted by C3PAOs.
- Access data when and where you need it: in the field and on-site.
- Video conference is encrypted in transit
- Mistake-proof devices: in case the device is lost or stolen no local permissions to the user prevent data leaking.
- Devices are purpose-built to be secured: the device wipes when the lid closes.
- Familiar office productivity tools for speedy user adoption and effective workflow.
- Quick implementation of CMMC controls to safeguard CUI and FCI to GET and KEEP contracts.
- Defense in depth offers peace of mind that your reputation is protected.

Why Use SecureCMMC™ Enclave?
- Verified by DIBCAC. SecureCMMC has passed many DIBCAC High Assessment many times, and is the solution used and trusted by C3PAOs.
- Access data when and where you need it: in the field and on-site.
- Video conference is encrypted in transit.
- Mistake-proof devices: in case the device is lost or stolen no local permissions to the user prevent data leaking.
- Devices are purpose-built to be secured: the device wipes when the lid closes.
- Familiar office productivity tools for speedy user adoption and effective workflow.
- Quick implementation of CMMC controls to safeguard CUI and FCI to GET and KEEP contracts.
- Defense in depth offers peace of mind that your reputation is protected.
Google Workspace Enclave
Over 80 State and Federal Agencies utilize Google Workspace.
Built-in Features Defense-in-Depth
-
Automatic updates
-
Sandboxing
-
Verified Boot
-
Data Encryption
-
Recovery Mode
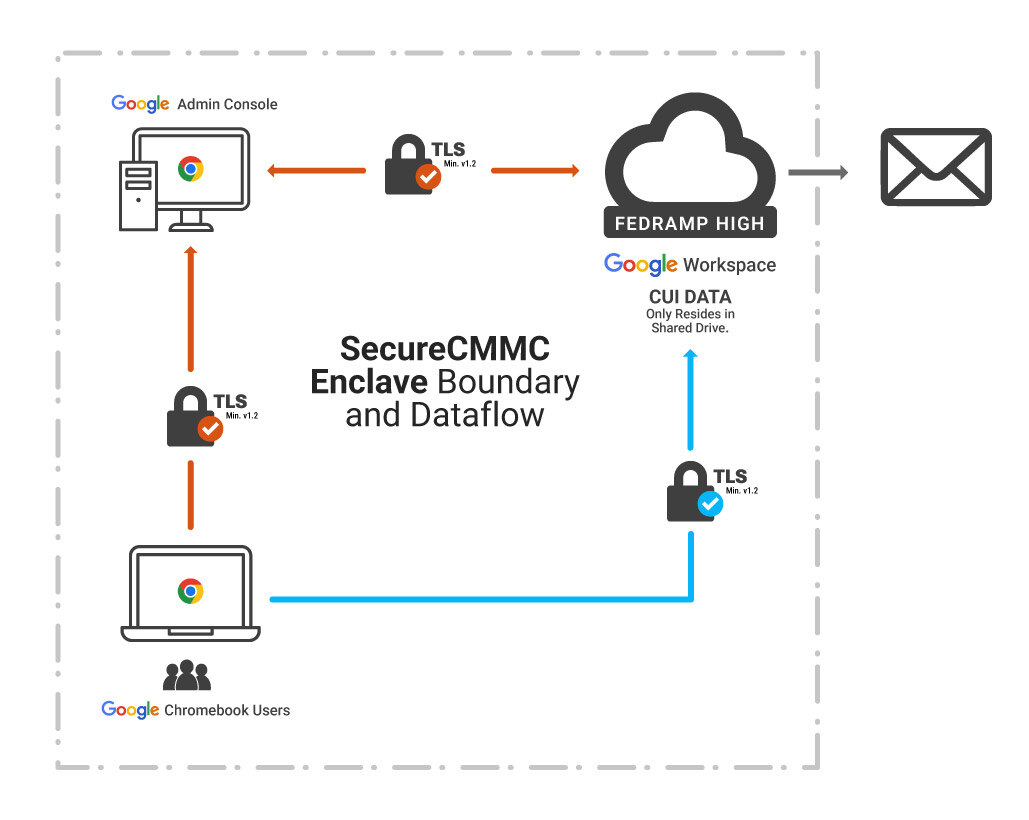

![]()
Features of BUILT SecureCMMC™ Enclave
CUI Secured in an Enclave Built for A/E/C
Are you an Architecture, Engineering, or Construction (A/E/C) firm operating within the Defense Industrial Base or its supply chain? To secure new defense contracts, you will need CMMC Certification at the time of award.
Navigating the complex and stringent CMMC compliance requirements can be particularly challenging in the A/E/C sector. It consumes valuable time and resources—time that could be better invested in designing, engineering, and building critical projects.
- Access data when and where you need it: in the field and on-site.
- Industry-Specific Secure Environment: Protect your blueprints, project plans, and Controlled Unclassified Information (CUI) with confidence.
- Zero Trust Principles: Enforce least privilege access through project and contract-level segmentation, ensuring only authorized team members can access sensitive data.
- Affordable licensing to meet project, contract and enterprise-level requirements.
- Technical support: keep your staff on task, not messing around in tech. MNS Group staff configure the devices and Workspace, train Administrators, and provide CMMC documentation.

Who Is An Enclave Right For?
There are many factors that contribute to whether CMMC compliance is best implemented through an enclave, or comprehensively to include the entire organization. Scoping how CUI flows within your business and who has access to that sensitive data will help you determine the viability of an enclave solution against essential constraints. MNS Group will guide you to the environment that will best suit your needs.
An enclave might be right for you if you:
- Are part of the DIB and Supply Chain and create, store, process, or transmit CUI
- Need to certify at CMMC Level 2
- Want to scale compliance implementation from enclave to enterprise over time
- Have limited technical or compliance SME resources
- May have a small percentage of staff that handle CUI within the larger enterprise
- Want to compete for contracts requiring CMMC ASAP





