Posted on Apr 10, 2020
The global pandemic is open-season for bad actors utilizing technology to prey on individuals. Several mechanisms are being employed where attackers profit from the crisis: phone calls (including robocalls), emails, text messages, fake and phishing websites, malicious ads on reputable sites, and fake apps. These scams/attacks vary greatly in content and sophistication and some may even be specific to a region or town. As always, be wary of any solicitation for personal and/or financial information related to COVID-19.
Read More »
Posted on Apr 4, 2020
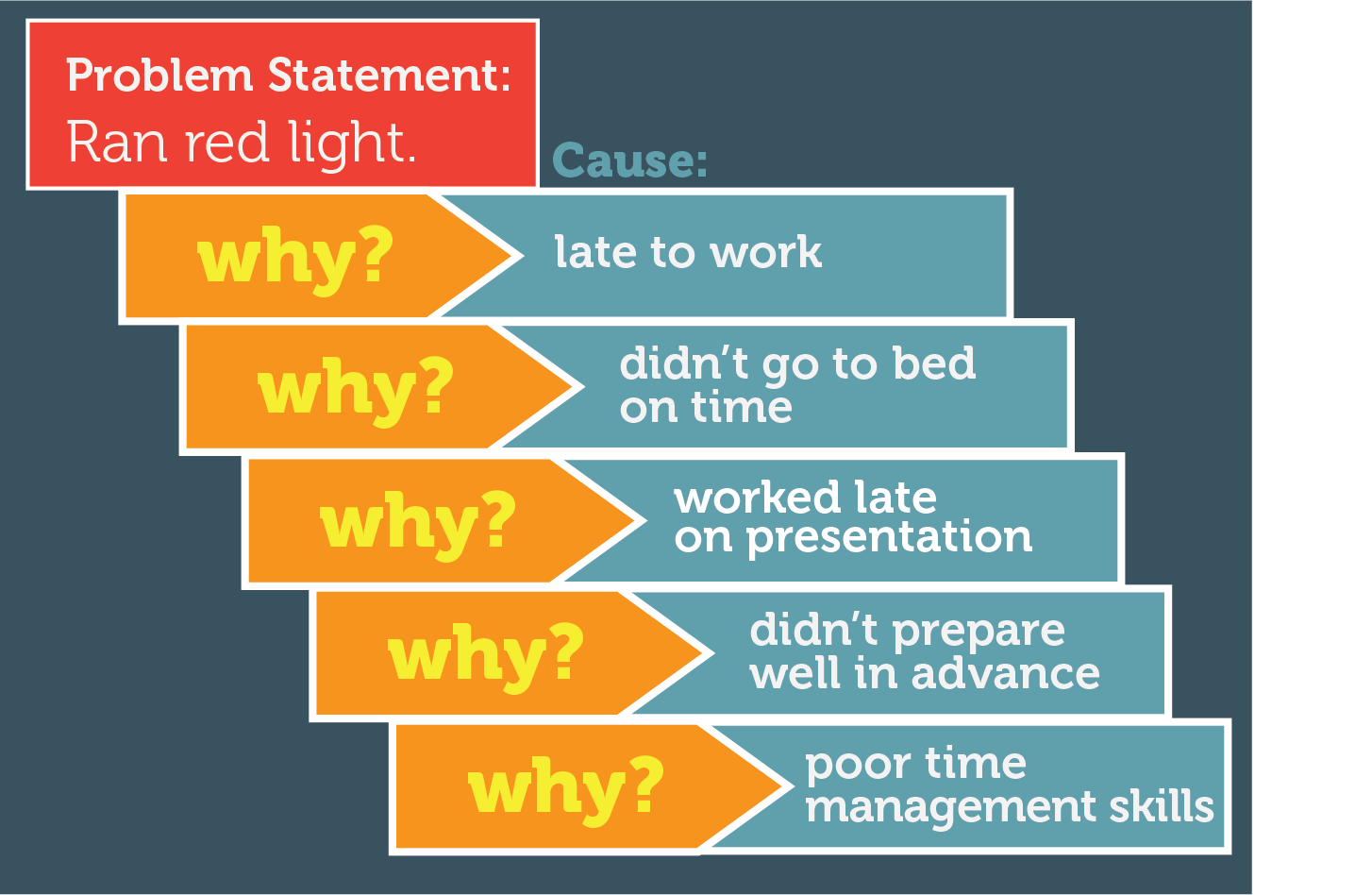
The Japanese industrialist Sakichi Toyodo, founder of Toyota Industries, developed a technique in the 1930s to identify root issues that inhibited success. He called it the 5 Whys. Toyota and many other organizations implement this Root cause analysis (RCA) technique today. Often as organizations grow, the management becomes removed from the day to day work that provides the value to the business. When problems arise, the leaders are not informed in a way that will equip them to make decisions to take appropriate counter-measures. This technique preserves precious time resouces because it avoids quick-fix solutions that may only solve a few symptoms and not the underlying problems.
Read More »
Posted on Feb 10, 2020
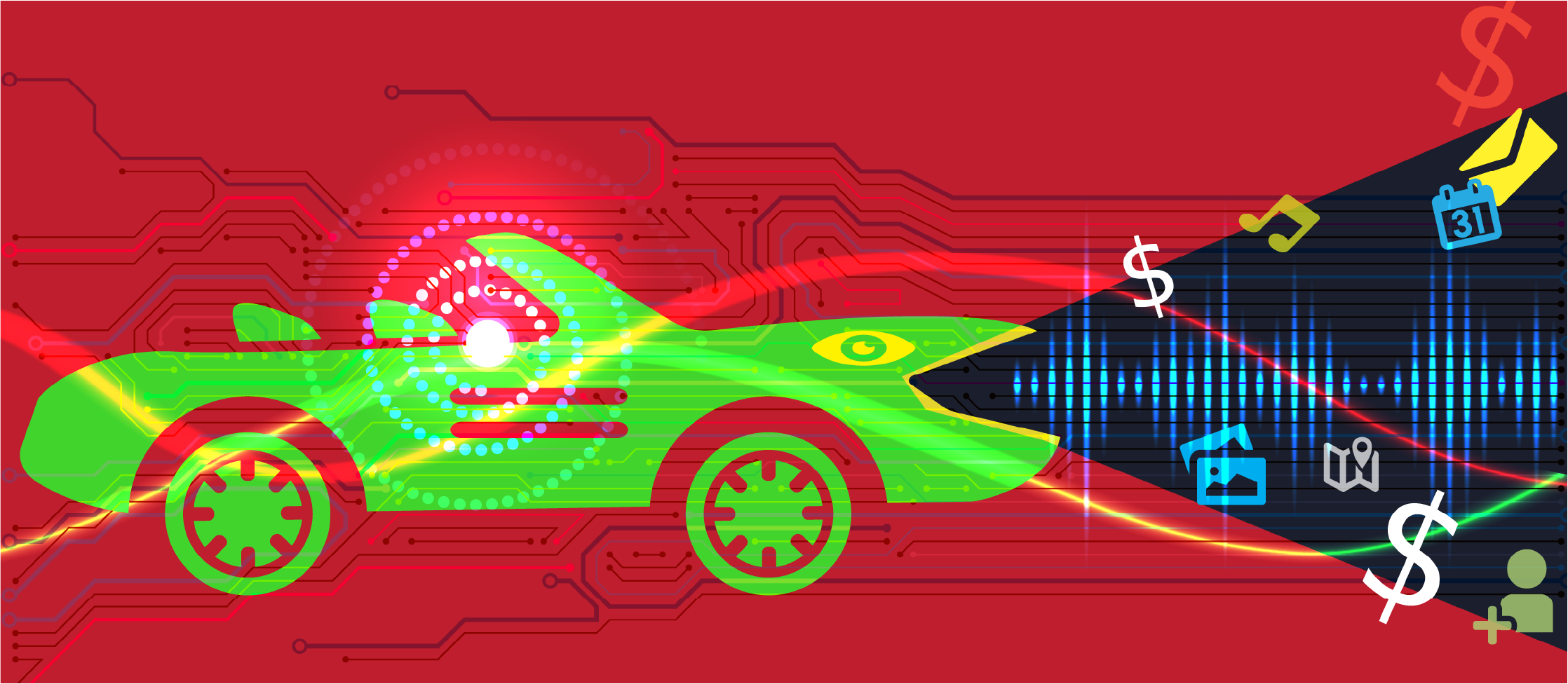
We have ALL been checking ALL the boxes that say we agree to privacy policies as they apply to our personal information, whether it be mobile phone contracts, applications like Facebook and other social media, and our vehicles. Wait – a privacy policy for our vehicles? When you plug in or connect your mobile device via Bluetooth a flood of information is downloaded and sent back to the car manufacturer over a continuously-on Internet connection. Car companies also send information to your vehicle, to fix bugs and add features. With 5G cellular networks being added all around the country, the amount of data moving to and from your vehicle is likely to increase. The difference between checking boxes for your smartphone, Nest or Alexa is that you KNOW those items are collecting data, but you likely didn’t realize that your car is also.
How much could your car possibly know about you? Turns out: quite a bit.
Read More »
Posted on Nov 1, 2019
Chances are you are considering an increase in your IT and security budget for 2020- and you are in good company.
Read More »
Posted on Sep 9, 2019
You are ready to invest in outsourced managed services to keep an eye on your network and secure your business: what are some of the questions your should be asking when you interview a potential partner?
Read More »
Posted on Jul 9, 2019
There are many scenarios that menace business executives in the restless pre-sleep: security breaches, wondering if their company’s credentials are for sale on the dark web, worrying over the impact of impending volatile weather, concerns over a dissatisfied or malicious employee, anxiety over old or failing equipment and the budget to replace them, the loss of a key employee.
Read More »