Which Group is Protecting Your Company?

Hiring a managed network service provider is like hiring an army, a military unit that protects your business from cyber attacks. But not all managed network service providers are alike. Even though they might be armed with similar equipment, some are like a rag-tag group of mercenaries, while others operate like a highly trained military unit.
This article covers what to look for when you hire a team to manage your technology.
As Regulated as the Roman Military
This kind of team operates like a well-ordered military unit.
- They implement structures and principles that are proven and effective.
- They have an established system that creates consistent results for you.
- When they engage a new client, they set up industry best practices and workflows for things like password policies, storage procedures, and maintenance protocols.
Standardizing these procedures creates a streamlined, organized workflow for both you and them.
How You Benefit
- Lower cost, faster service
You’re served more efficiently when there’s an issue because everything in your network has already been standardized. - Consistent results
Everyone on the support team is familiar with the configuration standards and how to resolve issues that occur. - Improved network security
Adhering to security best practices reduces the risk of hackers getting into your network. - Minimal business interruptions
If an issue occurs, the procedures allow for your staff to keep working while the problem is fixed. - Easier reporting
When you have to submit documents for security audits, insurance, or any other purpose, reports are simpler and more straightforward for you to prepare. - Higher profit
When your employees spend less time working with support, they spend more time working on mission-critical, profit-making activities.
Example Policies in Action
Here’s how we implement these policies at MNS Group.
- Password policy
We implement a consistent policy to address password complexity and frequency of change. - Program installation
We establish guidelines on how much freedom users have on their own computers, such as allowing them to install programs without going through an IT approval process. - Business continuity
If an employee’s computer crashes, they will be able to keep working from another computer because we’ve standardized the whole company’s network. - Defining expectations
We explain how to submit a support ticket and how we assess the issue. These parameters clarify expectations about communication in the partnership.
Everyone’s Secure
Our policies and procedures are applied to every single computer and user in your company. This includes all levels, from upper management to the employee. It’s important for your staff to understand why these “defense tactics” are essential. We help you explain to them what’s going to happen and why.
Our Processes, Your Profit
Our standardized procedures will ultimately give you better service at a lower cost. We save you money because you can spend more time working instead of dealing with IT issues. Our clients experience 67% less network problems than the industry average.
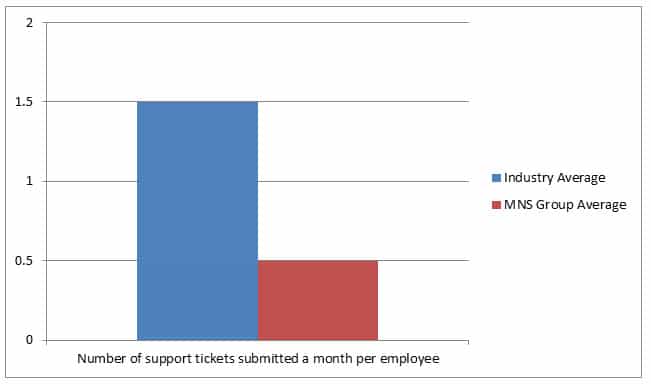
Abiding by established best practices keeps your network running as smoothly as possible. Don’t hire just anyone to protect your most valuable information. Hire a highly trained army, and your business will stay secure, productive, and efficient.






